You may have heard that you can restore a SharePoint Library or read an article mentioning this option. But when you try to find it, you realize it's not available.
In this article, I'll show you how to locate this option.
Here is a screenshot of the library that I messed up, and now I need to restore this entire Library. Let’s go to the settings and look at the menu. Take a look at the 'Library Settings' option—there’s nothing there. The 'Restore this Library' option is supposed to appear right below 'Library Settings,' but it is missing.
Now watch this:
We click on 'Library Settings' to open the settings.
Then click “More library settings”.
The settings page opens, but we won’t find our option here either. Instead, we’ll locate our library in the left panel—it’s 'Version Demo 2'—and navigate back to it. Let’s click on it.
We’re now back in the library where we started. But this time, if we go to the settings, the 'Restore this library' option has appeared right under 'Library Settings.'
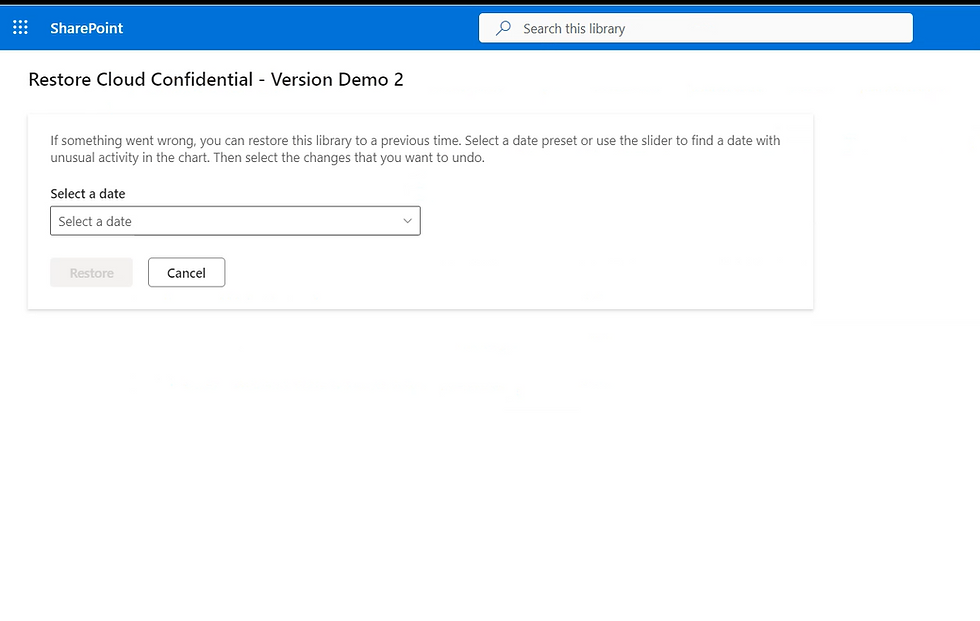
Let’s select 'Restore this library,' and as you can see, we’re now on the restore page.
If you decide to restore the library later and click Cancel, when you return to the library, you’ll have to go through the same acrobatics we just did to navigate back to the 'Restore' page. As you will see, the 'Restore this library' option has disappeared again.
If you do it one more time—notice that this behavior is consistent. You’ll have to use this workaround every time you need to restore the library, unless Microsoft fixes it.
Now that you know how to find this option, I caution you to use it carefully until you fully understand how it works. I’m preparing an article where I’ll show you how easy it is to mess up a library and lose all your files if you're not mindful of some quirks the Restore option has.
Watch the video that shows this behavior step-by-step: